Ransomware hits on logistics double in 2025, Cyble report reveals
The report reveals that ransomware syndicates launched 283 verified attacks against transport and logistics firms throughout the year.

The threat to the global supply chain has evolved beyond locked screens and encrypted files; it has moved to the physical theft of goods. A new report by Cyble reveals that the line between digital risk and physical security has fundamentally fractured in 2025.
The most alarming development for the cargo industry is the emergence of "cyber-enabled cargo theft". Intruders are no longer just holding data hostage; they are weaponising network access to locate, divert, and steal physical shipments.
This shift represents a dangerous new frontier for freight forwarders and fleet operators. The report highlights that criminal cartels are now utilising sophisticated Remote Monitoring and Management (RMM) tools to bridge the gap between IT networks and operational assets. By exploiting vulnerabilities in GPS trackers and operational technology (OT) systems, including those in rail networks, attackers can gain real-time visibility into the movement of goods. This "god mode" view allows them to track high-value loads, manipulate routing data, and even potentially disrupt vehicles remotely to facilitate physical robberies with surgical precision.
The report reveals that ransomware syndicates launched 283 verified attacks against transport and logistics firms throughout the year. This figure surpasses the combined total of incidents recorded in 2023 (120 attacks) and 2024 (122 attacks). The surge reveals a shift by criminal cartels to exploit the time-sensitive nature of trade for leverage. Disruption to these networks halts the movement of goods and impacts economies worldwide.
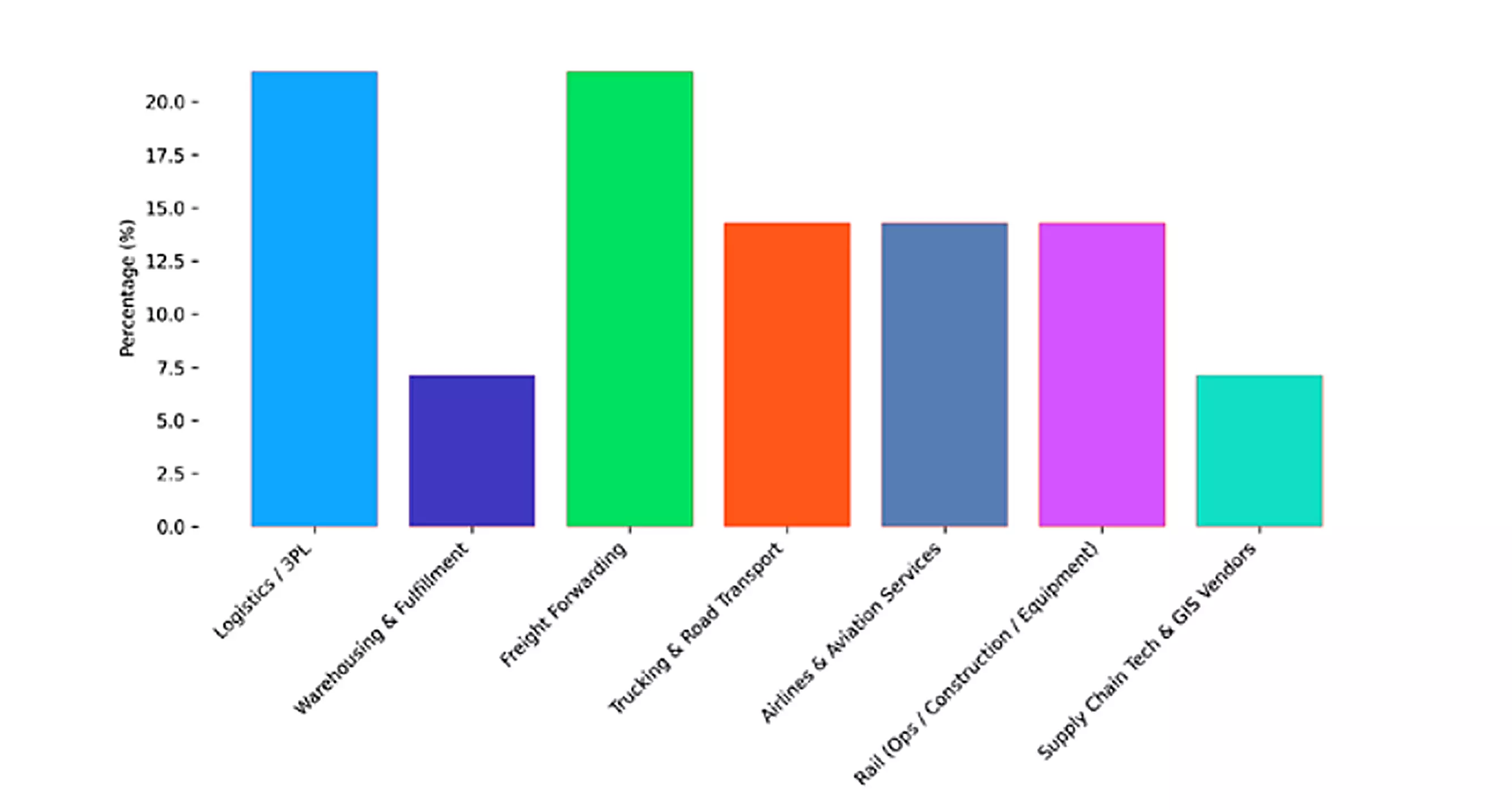
Four dominant ransomware groups drove this wave of instability. The report identifies CL0P, Qilin, Akira, and Play as the architects behind 57 percent of the observed incidents. CL0P emerged as the most prolific aggressor, responsible for 68 attacks, or nearly one in every four incidents. Their strategy relied on "concentrated bursts" of activity, exploiting vulnerabilities across dozens of victims simultaneously on single days like January 15 and February 24.
'Single days' refers to specific dates where attackers executed massive, simultaneous waves of compromises, hitting dozens of victims within a 24-hour window rather than spreading attacks out over time. In contrast, the Qilin group maintained a sustained operational tempo that intensified late in the year, particularly targeting European infrastructure.
The engine driving these mass exploitation events is a library of critical security flaws. The report highlights that the 2025 threat landscape was defined by the weaponisation of entries in the CISA Known Exploited Vulnerabilities (KEV) catalogue. The CISA KEV catalogue is a dynamic list maintained by the U.S. Cybersecurity and Infrastructure Security Agency that identifies security flaws confirmed to be actively exploited in the wild, serving as a priority patch list for organisations.
A significant majority of these exploited flaws carried CVSS scores of 9.0 or higher (critical severity vulnerabilities), granting attackers remote code execution capabilities without requiring authentication. Vendors central to enterprise infrastructure, such as Microsoft, Apple, Cisco, and Fortinet, were frequent targets. The report points to specific, devastating flaws like the critical vulnerability in Adobe Experience Manager, which allowed attackers to seize full control of systems. Similarly, vulnerabilities in Cisco’s Identity Services Engine were seen in active in-the-wild exploitation.
This means that cybercriminals are currently using a specific vulnerability to launch real attacks against operational systems on the open internet, rather than the flaw merely being a theoretical risk discovered in a controlled research environment. These flaws served as open doors for ransomware groups to bypass perimeter defences and lay siege to internal networks.
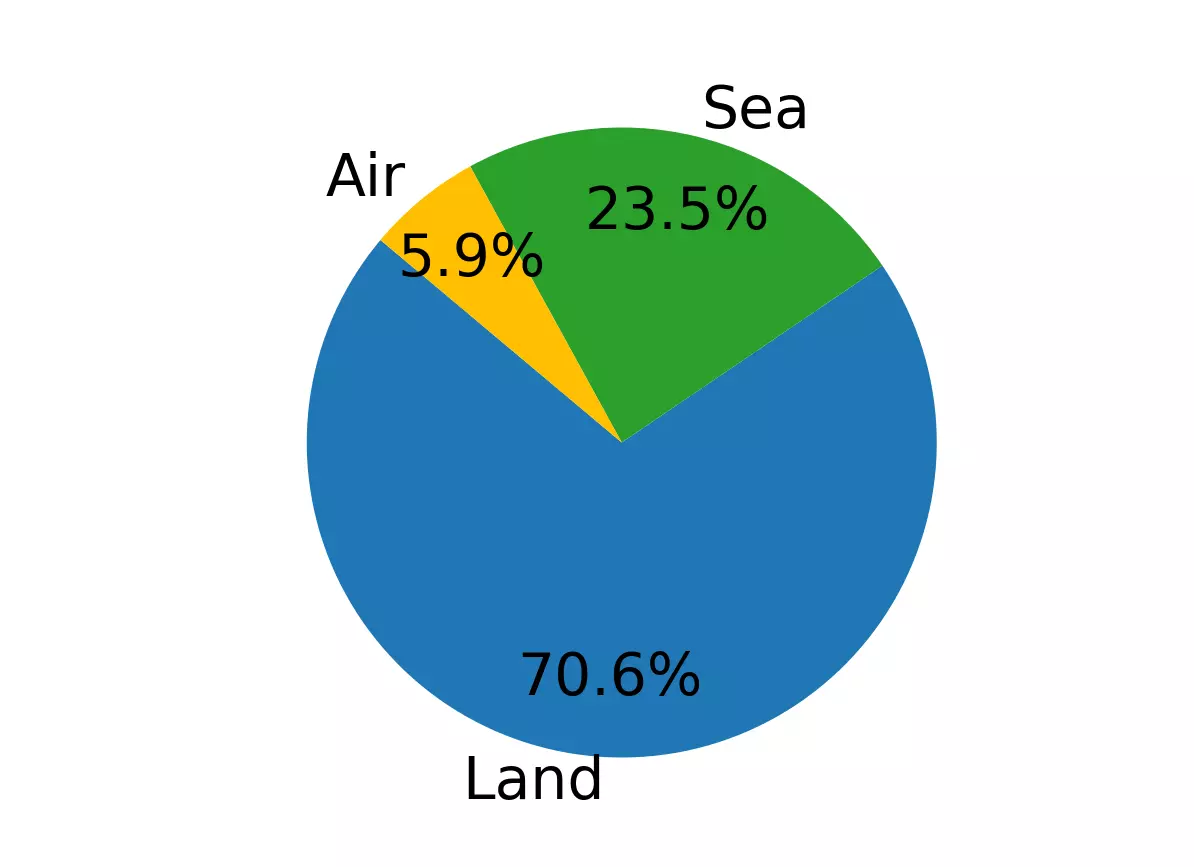
Land-based operations absorbed the brunt of this digital offencive. Trucking fleets and freight services accounted for nearly 71 percent of all ransomware victims, creating bottlenecks that ripple outward to ports and distribution hubs. The United States remained the primary theatre for these incursions with 140 confirmed attacks, but the threat also expanded into South America. Companies in Brazil, Colombia, and Chile appeared on victim lists, indicating that vital supply chains in emerging economies now face the same systemic risks as major industrial powers.
Intrusions also exposed millions of individuals to fraud. The group known as Scattered Spider breached a customer service portal belonging to Qantas, exposing the personal information of approximately 6 million travellers. In a separate incident, a threat actor advertised a database containing 7 million records allegedly stolen from a logistics platform in India. The Termite ransomware group further illustrated the financial risk by leaking sensitive budget reports and business plans from a UK-based supply chain management firm.
Geopolitical friction also spilt into the sector. Groups aligned with Ukraine claimed a destructive strike against the Russian carrier Aeroflot, alleging the destruction of 7,000 servers and the exfiltration of 12 terabytes of data. This incident resulted in flight cancellations and infrastructure damage, demonstrating how logistics hubs have now become active frontlines for geopolitical cyberwarfare.
For the cargo industry, the message is clear: cybersecurity is no longer just an IT issue—it is now a critical component of cargo security and loss prevention.
Cyble is a global AI-powered threat intelligence company providing organisations with real-time visibility into cyber threats through advanced research, dark web monitoring, attack surface management, and comprehensive security solutions. Cyble’s unified intelligence platform enables security teams to detect, respond to, and prevent cyberattacks before they cause significant damage.
Nikitha Sebastian
I'm a media professional with a background in journalism, psychology, and English, which provides me with a solid foundation in research, storytelling, and multimedia reporting. My diverse skill set spans writing, interviewing, and content creation with a deep understanding of human behaviour and communication.


